Organizations often struggle with data governance because their data privacy and information security programs may not be operating in full harmony. However, to truly manage data responsibly is to ensure that these two areas work as intertwined with each other as much as possible.
Data privacy focuses on how personal information is collected, used, and shared, while information security protects that data from emerging threats and unauthorized access. By combining these two domains, a robust data governance framework is formed, as they each handle different yet corresponding aspects of protecting and managing data. This synergy not only supports better policy alignment but also unifies risk management efforts and promotes effective cross-functional collaboration.
In this blog, let’s explore practical steps for aligning data privacy with information security for a more successful data governance program and reinforcing your organization’s overall data protection posture.
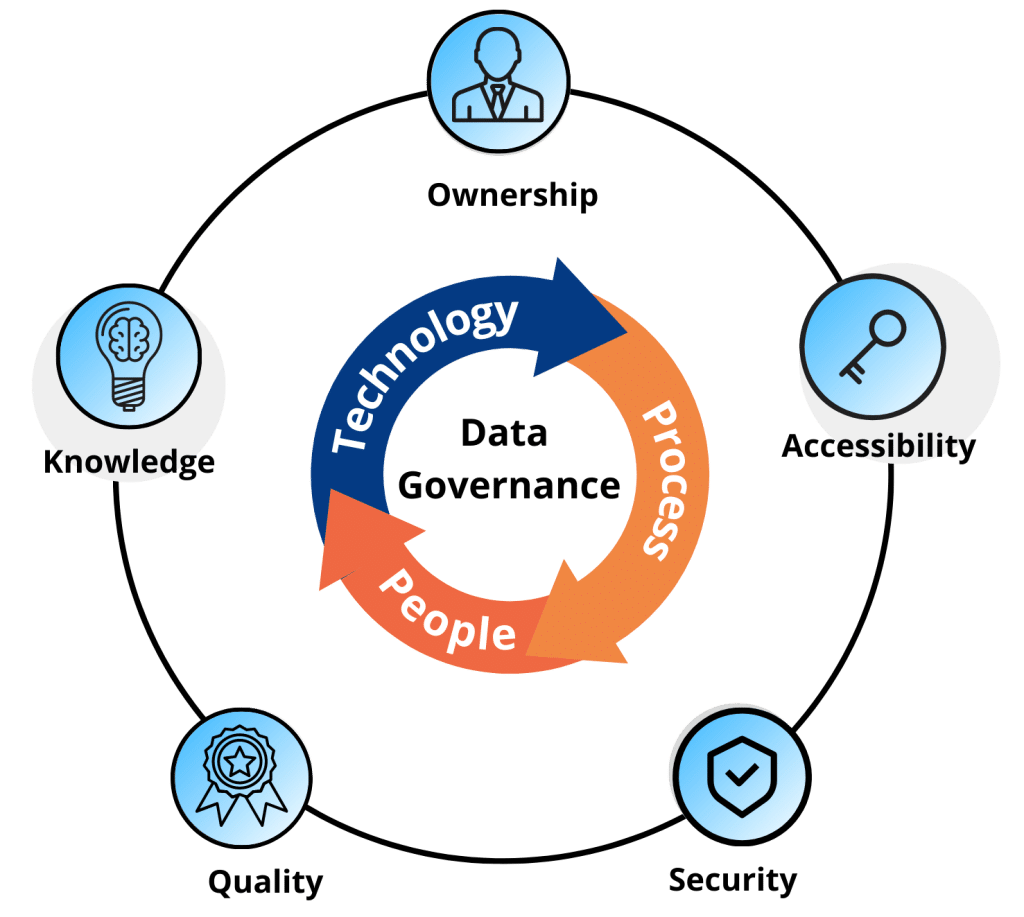
Practical Strategy #1: Utilize Data Mapping Across Data Privacy & Security to Strengthen Governance of Compliance, Accountability, & Ownership
A strong data governance framework requires both the strategy of data privacy with the execution of information security. Together, they create the foundation of a reliable governance program by outlining the rules, policies, and processes for managing data throughout its lifecycle.
This integration can be seen through comprehensive data mapping; the process of identifying and documenting where data exists, resides, flows, and who has access to it. This visibility helps stakeholders monitor vulnerabilities and map out unauthorized ownership, unifying data privacy and information security efforts.
- For data privacy, mapping is vital to help track and manage personal and sensitive data in a lawful and ethical manner. For example, data protection regulations such as GDPR, CCPA, or HIPAA enforce strict limitations on user access to data and require explicit consent to be obtained. These regulations demand a collaborative effort to ensure that compliance with privacy measures are accurately followed.
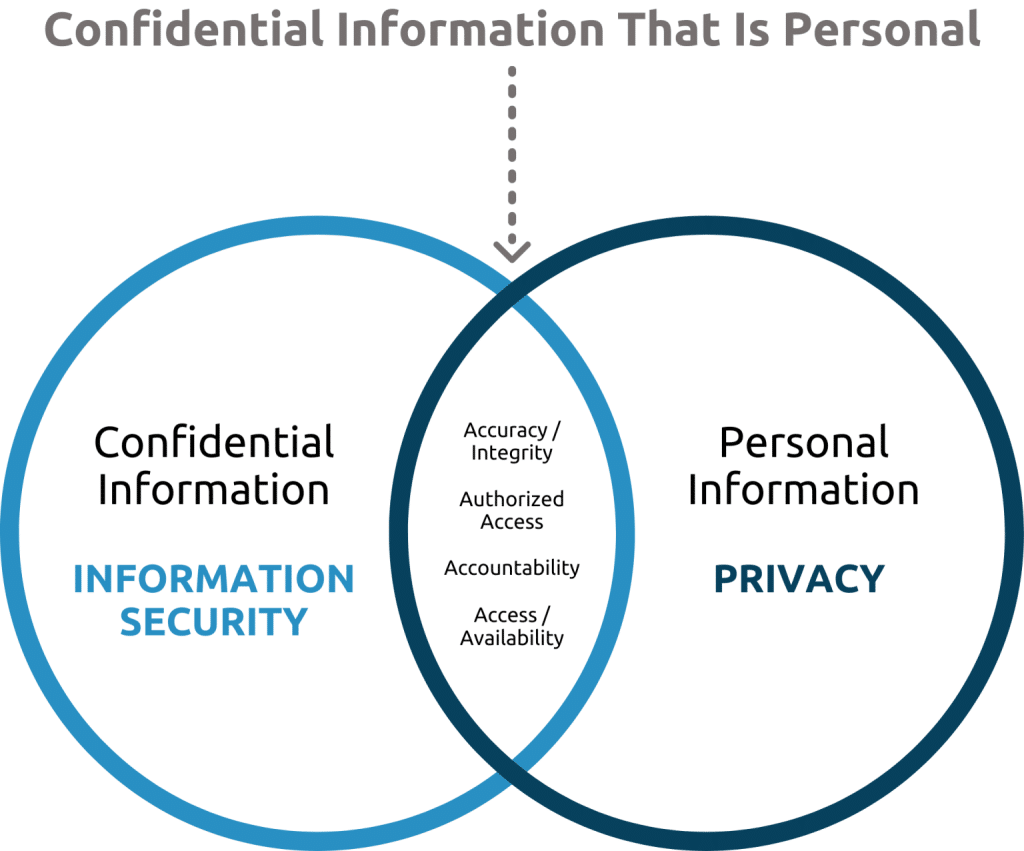
- Information security aligns alongside this as it applies protection controls, such as encryption and threat detection to any identified gaps and weaknesses. It protects all data gathered both personal and non personal with access controls that prevent unauthorized third-party exposure or breaches.
Through data mapping, each domain reinforces an organization’s ownership and accountability by clearly identifying who owns the data, who can access it, how long it is retained, and which controls are in place to protect it. Collectively, they can help reduce compliance gaps, monitor access, and enforce user permissions, resulting in a data governance program that is more accurate, and compliant with both internal and external standards.
Practical Strategy #2: Enhance Data Governance Through Cross-Functional Collaboration of Data Privacy & Information Security
It is essential for data privacy and information security teams to collaborate and share insights that address overlapping issues, rather than working independently and duplicating efforts. Cross-functional collaboration brings greater efficiency to day-to-day operations by streamlining workflows and increasing visibility and agility, especially when assisting one another with data risks and aiming for faster, coordinated response times.
Integrating data privacy and information security can enhance decision-making, strengthen risk management strategies, and provide holistic solutions to operational inefficiencies. For example, in the event of a breach like the Yale New Haven Health exposure on March 8th, 2025, that compromised the personal information of 5.6 million patients, it was a significant data breach that could have been avoided with the right oversight.
- The incident resulted from unauthorized access to a network server, revealing sensitive data of names, dates of birth, contact details, medical record numbers, etc. Although they were able to contain the breach and restore the affected systems, the initial situation itself could have been avoided or mitigated.

- A lawsuit filed against New Haven stated, “the data breach could have been easily prevented through standard practices (…) and encryption of all private information.” This highlights the importance of how better integration between data privacy and security teams could have empowered a more resilient response process to assess, detect, contain, and recover the breach with minimal risk.
With sufficient collaboration on access controls, assigned data ownership, and unified security measures, data privacy and security teams could have significantly reduced the likelihood of unauthorized access as well as addressed vulnerabilities proactively, rather than reactively.
Practical Strategy #3: Align your Security by Design and Privacy by Design Frameworks for Effective Data Governance
Security by Design and Privacy by Design are proactive frameworks that apply effective security and privacy measures into the development of an organization’s systems and processes from the get-go.
- Security by Design ensures systems are built with embedded security protections since inception, protecting against threats before they arise.
- Privacy by Design safeguards personal data throughout its lifecycle, asserting privacy practices into every stage of data collection, storage, and processing.
By aligning these frameworks, organizations can reduce risks and ensure data is managed responsibly. Additionally, these frameworks make it easier to adapt to evolving industry regulations, as organizations can quickly adjust controls in response to changes and ensure standards are met. This minimizes disruption and keeps your organization at a strategic advantage of always being ahead.
Key Overall Takeaways
- Integrating and aligning data privacy with information security helps enhance your organization’s overall data protection posture and builds a solid foundation for identifying and mitigating risks early on.
- By applying these practical strategies, your organization can overcome compliance issues and improve response times to threats, thus establishing a long-term, unified approach to achieving a successful data governance program.
Need more guidance? Take the next step in leveraging privacy engineering expertise!
Your organization’s data privacy can’t wait. At Myna, we offer:
- Customized Privacy Engineering Solutions
- Compliance-ready Frameworks
- Expert Implementation Support
- Ongoing Technical Guidance
For further expertise and/or additional insights on Privacy Engineering benefits, please explore our Solutions page. Our team of experts are ready to assist you in navigating the complexities of data privacy and in building secure, protected systems designed to your organization’s specific needs for optimal performance.
Ready to secure your data? Book a consultation with our privacy engineering experts today!
Contact Us
REFERENCES
Image 1: Google Images
Image 2: The Intersection of Data Privacy and Security | Myna Partners
Image 3: Google Images
Data Privacy and Information Security: The Intersection of Data Privacy and Security | Myna Partners
Data Mapping: Data Mapping: A Foundational Exercise for Privacy Compliance
Yale New Haven Health Case Study: Yale New Haven Health data breach exposes info of 5.6 million patients
Privacy by Design: Privacy Engineering Guide





