In this Privacy Engineering Guide, we will cover:
- What is Privacy Engineering and Why It Matters
- Core Principles of Modern Privacy Engineering
- Critical Challenges and Practical Solutions
- Implementation Best Practices
- Tools and Resources for Privacy Engineers

We all have high expectations of privacy, security, and confidentiality when sharing our personal information with an organization’s systems and services. As hackers become more sophisticated, personal data remains under constant risk, especially when an organization lacks the proper tools or resources needed to help safeguard private information and meet compliance requirements.
Therefore, it is critical that privacy is integrated within an organization’s technology; no longer optional but essential. With the proper security measures in place, personal data of all sorts can be safely collected, stored, and shared with greater assurance. Organizations and consumers can feel confident knowing their information is secure and protected.
In this blog, we will explore the benefits of Privacy Engineering and have a better understanding of how it helps businesses not only meet industry regulations but build trust knowing they can efficiently protect consumer’s personal data. By implementing solutions now, businesses are better prepared to solve current needs and are laying the groundwork for future readiness.
What is Privacy Engineering?
Embedded from the very beginning of system design and planning, this practice plays a pivotal role in helping organizations enhance security and protect personal information. This framework integrates privacy protection within an organization’s system, looking at the design, process, and day-to-day operations.
The Privacy Engineering process evaluates and improves the security measures in place and aims to minimize any potential breaches and/or risks from occurring now or in the future, as well as complying with industry best practices.
Key Principles of Privacy Engineering
Let’s dive into four key Privacy Engineering principles, outlining protocols and importance:
The following principles of Privacy Engineering are based on insights from “Privacy Sense, Privacy Made Simple”, unless otherwise noted.
PRIVACY BY DESIGN
- Privacy by Design ensures that privacy is integrated into technology, IT systems, services, and products from the beginning, the forefront to guarantee data protection. This approach suggests that Privacy should be a core consideration when building systems. Businesses must proactively identify areas for improvement to guarantee privacy measures are strong and not compromising overall security, both in minor or major ways.
- Through the underlying sectors of Privacy by Design, for example, “Proactive, not Reactive,” “Privacy as a Default Setting,” “Privacy Embedded into Design,” etc. organizations can gain insight and alter the structure of their processes and operations to streamline privacy considerations. (Source: Data Privacy Manager Blog)
DATA SECURITY
- Data security involves protecting digital information from unauthorized access throughout its entire lifecycle, utilizing measures such as encryption and access control. Organizations should take proper precautions to establish secure policies and procedures to prevent digital loss.
DATA PRIVACY
- Data Privacy gives individuals the right and control over their information as well as affirms that organizations comply with laws when processing and collecting their data.
DATA INTEGRITY
- Data integrity refers to the accuracy and/or reliability of data. By implementing regular audits or reviews of stored records, it helps to keep data unaltered and ensures any errors are detected. This is to correct any issues as soon as possible.
Top Challenges of Privacy Engineering
Outlined are the three key challenges faced in Privacy Engineering:

CHALLENGE 1: KEEPING UP WITH EVOLVING REGULATIONS
Data governance within an organization refers to the overall management of data, including the establishment of policies, procedures, and standards to maintain consistency and compliance.
As global privacy regulations evolve, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), California Consumer Privacy Act (CCPA), and others, organizations may struggle to remain up to date and comply with all new privacy regulations and laws.
SOLUTION 1: CONDUCTING REGULAR AUDITS & ASSESSMENTS
- Internal audits, risk assessments, and privacy impact assessments (PIAs) help to verify that data handling practices remain compliant.
- With these assessments, companies can identify gaps or areas that need adjustment in response to regulation changes. These guidelines and/or regulations are crucial for ensuring data privacy, security and protection.
CHALLENGE 2: ENSURE PROPER USE OF USER CONSENT
Organizations carry the burden to help users understand what data is being collected, how it is being used, and where it is stored.
This poses the challenge to ensure that users give adequate level of consent and/or trust and businesses need to ensure their use of data is legally compliant and that they are abiding by global regulations.
SOLUTION 2: PROVIDING USER CONTROL
- By providing clear consent options, users will feel empowered to effectively understand what data is collected and why. Users should have control over their own data and the ability to opt-in or out of specific features as they see fit.
- By being able to withdraw at any time allows users to build trust and ensure compliance with privacy regulations.
CHALLENGE 3: EMBRACING DATA MINIMIZATION
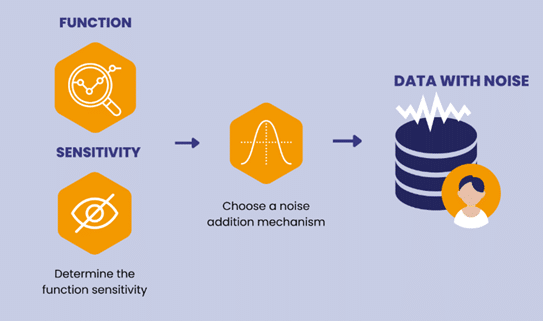
Data minimization is the practice of collecting only the data that is necessary for a specific purpose, thereby reducing the risk of unauthorized access. With this principle, organizations can limit the potential for privacy breaches by gathering only essential information for a specific purpose, limiting their exposure of risk.
SOLUTION 3: DIFFERENTIAL PRIVACY
- This solution enables the collection of useful data while protecting individual privacy. Apple’s Differential Privacy article describes a technique called “noise injection,” where random data is intentionally added to real user data before it is gathered or analyzed. This “noise” makes it impossible to link any individual’s information back to them.
- Through this method, organizations can examine patterns and statistics across large groups, such as how users interact with certain apps and can identify any trends without revealing a specific user’s personal details. This upholds the protection of privacy while still providing valuable data to improve services.
Best Practices of Privacy Engineering
Here are two of the best practices used for Privacy Engineering:
ENSURING PRIVACY BY DESIGN IS EMBEDDED IN DEVELOPMENT
- Organizations can ensure that privacy is embedded into the design and development of systems and applications from the beginning, by allowing privacy engineers to work closely with software developers, project managers, and system stakeholders to incorporate privacy into the development lifecycle.
AUTOMATING PRIVACY PRACTICES
- Organizations should find opportunities to invest in automation to manage lifecycle of personal information, such as honoring Privacy Rights from users.
- An example of effective automation would include the unification of consent collection and ingestion within a centralized system that becomes the source of truth for all preferences associated with a user within the organization.
Main Takeaways
All in all, effective Privacy Engineering practices are critical for organizations committed to safeguarding sensitive data and maintaining client trust. With the right guidance, businesses can confidently adhere to industry best practices and regulatory standards, while also building resilient privacy frameworks that can overcome evolving challenges.
Once the right policies, protocols, and solutions are in place, organizations can expect continuous compliance, operational efficiency, and data integrity.
Need More Advice? Take the Next Step in Privacy Engineering!
Your organization’s data privacy can’t wait. At Myna, we offer:
- Customized privacy engineering solutions
- Compliance-ready frameworks
- Expert implementation support
- Ongoing technical guidance
For further expertise and/or additional insights on Privacy Engineering, please explore our Solutions page. Our team of experts are ready to assist you in navigating the complexities of data privacy and in building secure, protected systems designed to your organization’s specific needs for optimal performance.
Ready to secure your data? Book a free consultation with our privacy engineering experts today!
Contact Us
References
Image 1 Source: Wire19
Privacy by Design: 7 Principles of Privacy by Design and Default – Data Privacy Manager
HIPAA Logo: LogoDix
CCPA Logo: Google Images
GDPR Logo: LoginRadius
Key Principles: What is Privacy Engineering: A Comprehensive Guide – PrivacySense.net
Privacy Impact Assessments: Privacy Impact Assessments | Homeland Security
Image 5 Source: Anonos
Apple’s “Differential Privacy” Article: Differential Privacy Overview





