In January 2020, the National Institute of Standards and Technology (NIST) released the first version of its Privacy Framework. The framework provides organizations with the means to enhance their internal procedures to fit their needs, and aims to assist organizations in building customer trust, fulfilling compliance obligations, and facilitating communication.
NIST believes that a “data-driven society has a tricky balancing act to perform: building innovative products and services that use personal data while still protecting people’s privacy.” Organizations must consider privacy throughout the development of all systems, products, or services. The challenge of complying with increasingly complex regulatory requirements is added incentive for adopting a framework of controls and processes to establish baseline practices that provide an adaptable model to mature privacy programs.
In this article, we examine the high-level structure of the NIST Privacy Framework, how the framework may support compliance efforts, and work in conjunction with the NIST Cybersecurity Framework to drive more robust data protection practices.
NIST Privacy Framework Overview
NIST divides the Privacy Framework into three major sections: Core, Profiles, and Implementation Tiers. The Core section identifies a set of privacy protection activities and organizes them into 5 functional groups:
1: Identify-P: Develop an understanding of privacy risk management to address risks that occur during the processing of individuals’ data.
2: Govern-P: Create a governance structure to manage risk priorities.
3: Control-P: Implement activities that allow organizations to manage data on a granular level while preventing privacy risks.
4: Communicate-P: Increase communication and transparency between organizations and individuals regarding data processing methods and related privacy risks.
5: Protect-P: Establish safeguards for data processing to avoid potential cybersecurity-related events that threaten the security or privacy of individuals’ data.
Each of these functions are further organized into categories and sub-categories that identify the set of activities supporting each of these functions. These categories and sub-categories can be used as references when establishing privacy program activities – i.e. privacy controls and processes – and showing the principles of privacy that they support.
The Profiles section explains outcomes of the selected functions, categories, and subcategories of desired processing activities. This allows an organization to gain a holistic understanding of their target privacy profile compared to their current privacy profile.
Once the target privacy profile is understood, organizations can begin to implement the necessary changes. The Implementation Tiers section breaks the process into 4 tiers, or degrees of adoption: Partial, Risk-informed (NIST’s minimum suggested action), Repeatable, Adaptable. These Implementation Tiers can provide useful information regarding current practices and whether those practices sufficiently address your organization’s risk management priorities.
Source: NIST Privacy Framework V.1.0
How the NIST Privacy Framework Overlaps with the NIST CSF Framework
Since its release in 2014, many organizations have utilized the NIST Cybersecurity Framework (CSF) to protect business information in critical infrastructures. The NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection.
However, while managing cybersecurity risk contributes to managing privacy risk, it is not sufficient on its own. Privacy risk can also arise by means unrelated to cybersecurity incidents. In turn, the Privacy Framework helps address privacy challenges not covered by the CSF.
- When aligned, they could help organizations achieve security and privacy goals more effectively by having a more complete view of the privacy risks.
- Organizations that have implemented the NIST CSF may be able to repurpose existing security workflows to align with the Privacy Framework without requiring a complete overhaul.
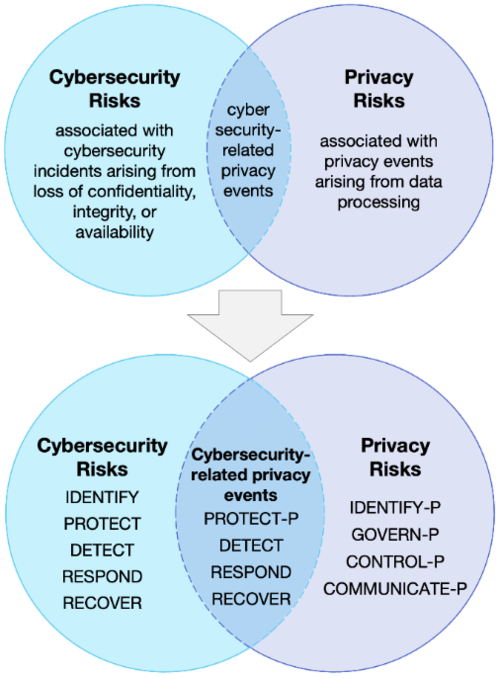
The graph below, provided by NIST, illustrates the overlap between cybersecurity risks and privacy risks. Although the core functions differ between the Privacy Framework and the CSF, the diagram illustrates the overlap where cybersecurity principles aid in the management of privacy risks and vice versa.
For an organization that has adopted the NIST CSF, certain cybersecurity controls already contribute to privacy risk management. When releasing a draft of the Privacy Framework, NIST indicated that the community that contributed to the Privacy Framework development highlighted the growing role that security plays in privacy management. In order to be useful for a modern privacy and data protection program, it is critical that organizations understand and utilize a framework that has the flexibility to include the security domains that are indispensable for maintaining good privacy practices.
How the NIST Privacy Framework Complements CCPA & GDPR
As global privacy standards and laws have matured, particularly with the introduction of the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR), organizations have been challenged with developing practices that address privacy requirements mandated by these regulations. Many organizations have developed robust programs and compliance processes, but these processes often operate in a siloed manner, depending on the region.
While the NIST Privacy Framework is intended to be “regulation-agnostic”, it does draw from both GDPR and CCPA and can serve as a baseline for compliance efforts. The Privacy Framework provides organizations a foundation to build their privacy program from by applying the framework’s five Core Functions. Even organizations with a well-developed privacy program can benefit from this approach to identify any potential gaps within their existing privacy program and components that can be further matured.
The following guidelines can help organizations apply the NIST Privacy Framework to fulfill their current compliance obligations:
Map your universe of compliance obligations: Identify the applicable regulatory requirements your organization faces (e.g., CCPA, GDPR) and map those requirements to the NIST Privacy Framework.
- This exercise can help organizations organize their approach for complying with privacy requirements and create a shared understanding of practices across regulations, including notice, consent, data subject rights, privacy by design, etc.
- Organizations will then benefit from a rationalized approach across all applicable regulations and standards. Organizations can then eliminate duplicated efforts and provide coverage across multiple and overlapping regulations.
Identify specific practices that support compliance obligations: Once your organization has identified applicable laws and regulations, privacy controls that support compliance can be identified.
- For early-stage programs, it may help to partner with key stakeholders (e.g., IT, marketing, product) to identify existing privacy controls and their effectiveness. Ultimately, controls should be designed to help organizations demonstrate that personal information is being handled properly.
Map current practices to the NIST Framework and remediate gaps: By mapping the existing practices identified to a category/sub-category in the NIST framework, your organization can better understand which of the controls are in place (and effective) and those controls that should be implemented or enhanced.
- Remediation efforts can then be organized in order to establish the missing controls, such as developing policies or procedures to address a specific requirement.
Establish a monitoring plan and audit controls: A vital part to your organization’s ability to demonstrate compliance with applicable regulations is to develop a process for evaluating the effectiveness of controls.
- Some organizations may be able to leverage existing Governance, Risk, and Compliance (GRC) tools that provide the capabilities to assess controls and report on program maturity.
- Frequency and type of monitoring will depend on the organization’s risk appetite and resources.
Ultimately, organizations will continue to be faced with the challenging and evolving privacy regulatory environment; however, the NIST Privacy Framework can be the first step in developing an enterprise-wide risk management program that balances business objectives with the protection of personal information.
Conclusion
The privacy regulatory environment is simple if viewed from the fundamental right of an individual’s privacy, but complex when organizations need to act on those requirements.
The NIST Privacy Framework intends to provide organizations a framework that can adapt to the variety of privacy and security requirements organizations face. The Privacy Framework’s inherent flexibility offers organizations an opportunity to align existing regulations and standards (e.g., CCPA, GDPR, NIST CSF) and better manage privacy and cybersecurity risk collectively.
Once adopted and implemented, organizations of all sizes can achieve greater privacy for their programs, culminating in the protection of personal information.



