Avoiding an FTC Request Order
Consumer trust is more important than ever. Yet, despite increasing oversight and ever-evolving regulations, many businesses still find themselves facing Federal Trade Commission (“FTC”) request orders. The FTC routinely investigates and takes enforcement action against organizations that fail to protect consumer data or mislead their customers. While some violations may be obvious, others branch from a lack of awareness or failure to keep up with changing compliance requirements. As regulations tighten, businesses that ignore or delay addressing recurring security or privacy issues are more likely to be targets on the FTC’s radar. So, why do so many organizations end up with an FTC order? And more importantly, how can you avoid becoming one of them?

In this blog, let’s explore what an FTC request order is, why your organization should care about avoiding one, and what you can learn from an organization that didn’t. Using a recent high-profile case involving GoDaddy, we’ll look at the consequences of neglecting basic security protocols and what you should be doing differently to protect your business.
What is an FTC Request Order & Why Should You Care?
When the FTC suspects a company may be violating consumer protection laws or privacy rules, such as mishandling personal data, neglecting data security obligations, misleading consumers, or engaging in questionable practices – it can issue an FTC order. A request order is a serious legal action that typically demands businesses to provide detailed information or evidence for the FTC to evaluate a company’s internal operations.
The FTC’s mission is simple: to protect consumers and hold organizations legally accountable to comply when they fail to do so. Receiving an FTC order can jeopardize your company’s reputation, lead to costly penalties, and even result in years of long-term federal monitoring and oversight until necessary compliance standards are met and current practices have improved.
Case Study: GoDaddy & The 2025 FTC Enforcement Action
To illustrate the ways in which the FTC enforces their rules and orders, let’s look at a recent case from January 2025 involving GoDaddy, a major web hosting online platform used by millions of businesses and individuals worldwide to keep their websites online and secure.
The FTC issued an enforcement order against GoDaddy after the company failed to implement basic security measures that could’ve protected sensitive customer data. In addition, GoDaddy made misleading claims about its compliance with the “EU-U.S. and Swiss-U.S. Privacy Shield Frameworks” and advertised itself as providing trusted security practices to consumers. The FTC found all these claims to be inaccurate and deceptive.
Below are some major factors that contributed to GoDaddy’s failures and what your organization can do to avoid making the same mistakes.
1. Lack of Multi-Factor Authentication (MFA)
GoDaddy failed to require additional layers of verification steps, such as using an authentication app, beyond just a username and password to secure their systems. According to the FTC complaint, “GoDaddy has also not offered MFA as an option to customers for their cPanel administration logins” (page 10). This leaves consumer data vulnerable and easily obtainable to unauthorized access.
What Your Organization Should Do Differently: Implement MFA for all system access. Don’t rely solely on usernames and passwords, require a second layer of verification through an authenticator app to significantly reduce the risk of a breach.
2. Inadequate Software Updates & Patch Management
GoDaddy neglected to maintain or apply software updates and security patches on a regulatory basis. The FTC found that “GoDaddy has failed to centrally track whether operating systems and other software are current with necessary security patches” (page 8). GoDaddy avoiding performing timely updates and left any prior security weaknesses exposed and unpatched. This allowed hackers to exploit old vulnerabilities and breach the entirety of their infrastructure.
What To Do for Your Organization: Enforce a regular schedule and/or cadence for updates and patches. Establish a patch management policy and consistently track or audit the status of all systems to ensure the latest software updates have been applied.
3. Poor Logging & Monitoring
The FTC claimed GoDaddy “failed to adequately monitor for suspicious activity and security threats,” and “GoDaddy failed to consistently store logging data in its central log repository (…). As a result, GoDaddy security staff could not readily access logged information to analyze or investigate suspicious activity” (page 9). As noted, GoDaddy had logs that existed but failed to store them properly in one central area, making the logs inaccessible when needed. Security teams were unable to effectively detect cyberattacks and trace how attackers got in or point to which systems were affected.
What To Do for Your Organization: Make sure all essential logs are consistently stored and saved into one central area in which teams can easily access them, for quick monitoring and investigation of security issues. Also, ensure logs are kept for at least one year or longer, as required by your internal policies.
4. Insufficient Segmentation of Hosting Environments
Between 2019 and 2022, GoDaddy experienced multiple data breaches in its shared web hosting environment. GoDaddy’s most sensitive systems were not properly separated from the rest of the interconnected environment, and this is where thousands of customer websites are stored on the same servers. According to the FTC, “GoDaddy has failed to adequately segment its Shared Hosting environment from less-secure portions of its network” (…). GoDaddy thus exposed its Share Hosting customers to the security weaknesses of its most careless Customer-Managed customers, and a threat actor in fact exploited this weakness to move between environments” (page 10).
Without isolating systems into different zones, attacks were not effectively contained, allowing hackers to move freely in accessing critical customer data. With GoDaddy’s environment offering little resistance, the overall impact of the breach had greatly increased.
What To Do for Your Organization: Properly isolate your systems to contain and limit the spread of attacks. Segment sensitive systems to ensure a breach in one area doesn’t lead to the exposure of the entire network.
5. Misleading Claims of GoDaddy Services
GoDaddy had advertised its services as “award-winning security,” but had failed to perform sufficient security practices on these claims and was falsely marketing the level of protection they offer to consumers.
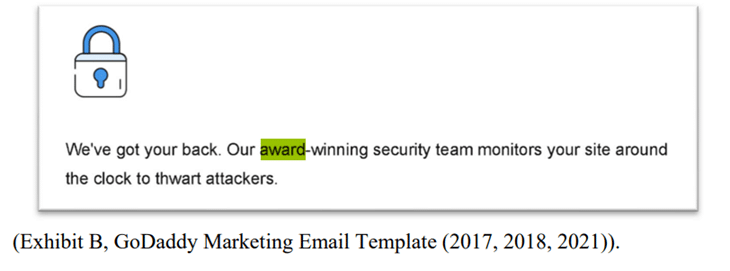

What To Do for Your Organization: Don’t market your company as a trusted, secure hosting provider if you cannot back this claim. You need to be transparent when demonstrating your security practices to earn consumer trust and loyalty. Misleading claims lead to FTC investigations and overall consequences, ensure your marketing is accurate and reflective of the actual security measures or practices you have in place.
Proposed Order Requirements – Noted by the FTC
Based on GoDaddy’s repeated inefficiencies and flagged practices, the FTC’s proposed overall order aims to prevent future misrepresentations from GoDaddy towards its customers and enforces the company to implement and maintain reasonable security moving forward.
The order outlines the following requirements:
- “Prohibit GoDaddy from making misrepresentations about its security and the extent to which it complies with any privacy or security program sponsored by a government, self-regulatory, or standard-setting organization, including the EU-U.S. and Swiss-U.S. Privacy Shield Frameworks;
- Require GoDaddy to establish and implement a comprehensive information-security program that protects the security, confidentiality, and integrity of its website-hosting services; and
- Mandate that GoDaddy hire an independent third-party assessor who conducts an initial and biennial review of its information-security program.”
Additionally, the FTC issued a formal order requiring GoDaddy to undergo a 20-year compliance monitoring period, “This Order will terminate 20 years from the date of its issuance (…) or 20 years from the most recent date that the United States or the Commission files a complaint (with or without an accompanying settlement) in federal court alleging any violation of this Order” (page 13). Meaning GoDaddy must adhere to these requirements and maintain compliance over time. If GoDaddy fails to comply, additional penalties may be enforced.
Conclusion
Any organization that handles sensitive data or offers online services is not immune to FTC rules and regulations. The GoDaddy case is a clear reminder that underscores the importance of what’s at stake when security practices are violated.
Some key takeaways:
- Be transparent and don’t mispresent or mislead claims to your customers. There is no benefit to this, and it will lead to FTC investigations, fines, and reputational damage.
- Understand that compliance is not optional in how you conduct daily operations, ensure privacy practices adhere closely to FTC expectations and stay current with new FTC guidelines.
- Take proactive steps and implement preventative measures now before having to pay the price later on.
As Samuel Levine, Director of the FTC’s Bureau of Consumer Protection, notes, “The FTC is acting today to ensure that companies like GoDaddy bolster their security systems to protect consumers around the globe.” Ultimately, being committed to consumer protection will not only help your organization stay off the FTC’s list but also will demonstrate that your organization operates with integrity and accountability while also prioritizing security on a day-to-day basis.
Not sure if your business meets FTC expectations or guidelines? Connect with our experts at Myna today for support in assessing and/or strengthening your current data protection practices, so you can remain current and fully compliant!
Contact Us
References
Image 1: Google Images
FTC: Federal Trade Commission | Protecting America’s Consumers
FTC Mission: About the FTC | Federal Trade Commission
GoDaddy Domain: Domain Names, Websites, Hosting & Online Marketing Tools – GoDaddy
FTC’s Case Against GoDaddy: FTC Takes Action Against GoDaddy for Alleged Lax Data Security for Its Website Hosting Services | Federal Trade Commission
Complaint of the GoDaddy Case and Image(s) 2 & 3





